In this article, I will talk about How to Store Cross-Chain Tokens Securely With Cross-Chain Tokens I will cover their best methods and procedures in fortifying one’s digital assets.
Learn to handle custodial and non-custodial wallets, enforce multi-factor auth, protect your mnemonic phrases, and mitigate common attack vectors. These methodologies will help you maintain your peace of mind when dealing with your Cross-Chain Tokens.
Understanding Cross-Chain Tokens
Cross-chain tokens are type of digital assets designed to transact and interact on multilpe blockchain networks.
Unlike other standard tokens which are confined to a single blockchain, cross-chain tokens devoid of intermediaries enable the use, transfer and trading of assets on different platforms.

This type of blockchain innovation increases liquidity, investment opportunities, or adoption of decentralized applications spanning blockchains.
Wrapped tokens, such as Wrapped Bitcoin (WBTC), and cross-chain stablecoins are a few examples. Despite the cross-chain tokens innovation and flexibility, their security challenges are unique cross-chain tokens are users store digital assets and wallets.
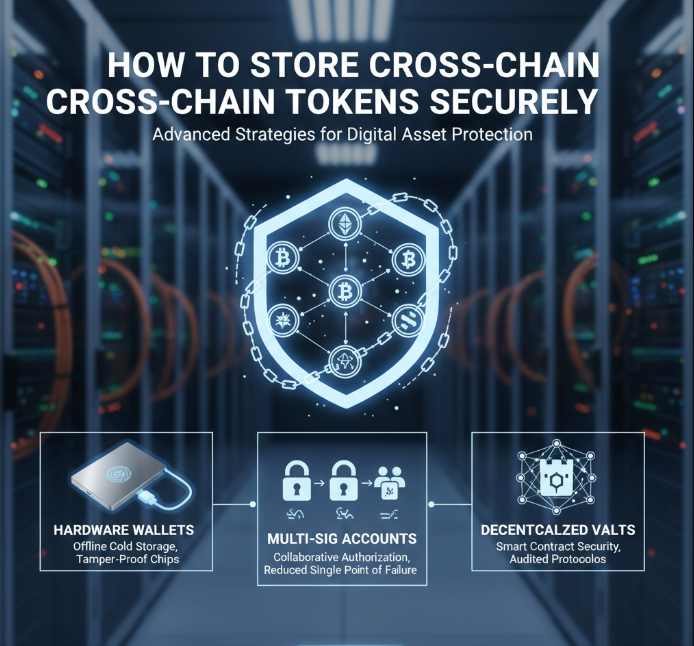
How to Store Cross-Chain Tokens Securely
Securely Store Cross Chain Tokens Using Ledger Nano X Example
Step 1: Choose a Reputable Wallet
For cross-chain tokens, hardware wallets that support several blockchains are Ledger Nano X, Trezor, and SafePal.
Step 2: Wallet Configuration
- Remove the wallet from the box and set it up using the guidelines from the manufacturer.
- After developing a new wallet, write the secret phrase down and secure the document (12–24 words).
- The secret phrase must never be stored electronically or over the internet.
Step 3: Install the Wallet Applications
- For Ledger Nano X and other wallets, use the corresponding applications (e.g. Ledger Live) to install apps on the blockchains that will hold the tokens.
Step 4: Send The Cross-Chain Tokens
- Using a computer or phone, connect to the wallet.
- Send cross-chain tokens from another wallets or an exchange to the hardware wallet address.
- Ensure you verify the network and the tokens before sending.
Step 5: Apply The Security Features
- Add a hardware wallet passcode.
- All attached apps should have 2-factor authentication (2FA) enabled.
Step 6: Make a backup of the seed phrase and store it securely
- Protect the seed phrase and store it in an offline medium such as a fireproof safe.
- Using metal backup offer an extra layer of protection for physical damage.
Step 7: Monitor the system and make updates whenever necessary
- Update the wallet firmware and associated application on a continuous basis.
- Transactions and balance can be monitored regularly for any anomalies.
Why Store Cross-Chain Tokens Securely
Protection from Losses: Cross-chain tokens are usually targeted as a result of their value. Keeping them securely reduces chances of them being hacked.
Avoid Loss of Funds: Tokens are subject to a permanent loss as a result of theft, improper management, loss of keys, lack of attention, or phishing scams.
Safety of Interoperability: As cross-chain tokens operate around several different systems, floating freely, unsafely, or lacking proper management, they put the holder at several weak points.
Dominion Over Holdings: Tokens kept in secured wallets provide full access and ownership fully unlike wallets in the exchange.
Stress Alleviation: Properly managing and securing the tokens to ensure the investment are kept safe can reduce considerable financial losses and stress.
Best Practices for Secure Storage
Use Hardware Wallets
Ledger or Trezor devices store tokens offline preventing online hacks.
Choose Renowned Software Wallets
Trusted wallets should always be updated and support multi-chain tokens.
Enable Two-Step Verification (2SV)
Software wallets and exchanges have another layer of protection added.
Protection of Seed Phrases
Backup phrases should be stored in a physical and fireproof box; digital copies are not secure.
Never Keep Funds in an Exchange
They are predominantly targeted for hacks; always retain a small amount for trading.
Update Wallets On A Regular Basis
Patching vulnerabilities associated with firmware and apps.
Use Multi Signature Wallets
Greater security is offered with multiple required approvals for a transaction.
Risks of Storing Cross-Chain Tokens

Hacking and Cyber Attacks
Cyber thieves can break into exchange accounts and wallets and steal tokens.
Phishing Scams
Users can be duped into giving away sensitive information like private keys and seed phrases through cleverly crafted scam emails and websites.
Loss of Private Keys
If a user forgets or puts private keys and phrases away, tokens, in this case, cross-chain tokens, can be lost forever.
Vulnerable Smart Contracts
Some attackers might take advantage of exposed cross-chain tokens overlooked in coding certain smart contracts.
Network Compatibility Issues
Tokens sent to incorrect blockchain networks can result in permanent loss.
Exchange Risks
With cross-platform tokens on centralized exchanges, the risk of mismanagement or insolvency can lead to loss of your tokens.
Additional Security Tips
Keep Software Updated
Make sure that vulnerabilities that could be exploited don’t go unaddressed.
Use Cold Storage
Online wallets can be funded with minimal amounts while the larger share of the tokens is kept offline.
Beware of Phishing Attempts
URLs, Emails, QR codes with tokens, Emails, and QR codes should be double-checked.
Enable Multi-Signature Wallets
Require additional approvals which reduces the chances of losing your money with a single transaction.
Segment Your Holdings
To limit the amount you could lose in the event of something being compromised, have several wallets.
Regularly Monitor Accounts
Stay vigilant and suspicious of unusual changes, hrefed your balances and your transactions.
Avoid Public Wi-Fi
Only complete these funds on a safe and private network.
Conclusion
The secure storage of cross-chain tokens is of utmost importance in order to eliminate the risk of hacks, scams, or loss of the digital assets. Investors can achieve control and peace of mind by using two-factor authentication, secure hardware wallets, reputable software wallets, and best practices such as the safekeeping of seed phrases, multi-signature setups, and regular updates.
Optimized security measures prevent loss of finances and ease the transactions of tokens across various blockchain networks. It is the prioritization of security that allows safe and secure management of cross-chain tokens, maximizing the value while minimizing most risk exposures.
FAQ
While possible, storing tokens on exchanges is risky due to hacking and insolvency threats. It’s better to use a personal wallet.
A seed phrase is a set of words that acts as a backup for your wallet. Losing it can mean permanent loss of tokens.
Yes, if you choose reputable wallets with multi-chain support and enable security features like 2FA.
Always double-check the network, token type, and wallet address before sending to avoid irreversible loss.
Multi-signature wallets require multiple approvals for transactions, providing an extra layer of security, especially for large holdings.